As electric vehicles surge in popularity, researchers want to learn more about the vulnerabilities of public-use charging stations and the risks of fast charging technology.
If you drive an electric vehicle (EV), your future trips to the charging station may be quicker thanks to up-and-coming charging technologies, but they could also result in an uninvited stowaway: a computer virus.
While most EV owners charge their vehicle batteries overnight in a garage at home, longer journeys require “filling up” at a public station. Those public stations, while convenient and necessary, pose a different set of problems – time being one of them. Taking your battery electric vehicle (BEV) from empty to full at a public charging station can take upwards of 12 hours.
The slow-charging dilemma has inspired researchers to create a quicker solution: extremely fast charging (XFC). A recent article from New Atlas reports that scientists from China have created XFC technology that can get a lithium-ion battery to 60 percent charge in under six minutes. Implementing this fast charging technology may seem like a no-brainer, but this improved feature could come with risks to consumers.
Ryan Gerdes, associate professor in the Bradley Department of Electrical and Computer Engineering (ECE), and a team of student and faculty researchers are curious to learn more about the vulnerabilities of these public-use charging stations, the risks of XFC, and the fallout for EV drivers if they are exposed to cyberattacks.

The EV surge
According to the U.S. Department of Energy (DOE) Alternative Fuels Data Center, the United States has more than 46,000 public electric vehicle charging stations, with a total of over 115,000 individual electrical vehicle supply equipment (EVSE) charging ports.
Recent data also suggest that in the past few years, EVs and plug-in hybrid electric vehicles have increased in popularity among American consumers. Sales of these vehicles nearly doubled from 308,000 in 2020 to 608,000 in 2021. Of last year’s purchases, EVs accounted for 73 percent of all plug-in electric vehicle sales.
Having more alternative fuel vehicles on the road increases demand for charging stations. However, having more stations gives hackers the opportunity to compromise these technologies on a larger scale. Furthermore, implementing XFC will require coordination between the U.S. grid, charging stations, and electric vehicles themselves, which could increase the risk of cyberattacks at multiple levels. For the consumer, this means hackers could potentially access credit card information, driving data, GPS location, and other sensitive material.
To combat these potential threats, Gerdes has been awarded $2.5 million by the DOE to analyze the risks of XFC and cyberattacks. In addition, Ford has provided two Mustang Mach-Es, the company’s newest electric vehicle model, to put EV cybersecurity to the test.
“When we told Ford about the research we wanted to perform, they said we should be using the most up-to-date vehicles available to show the strengths and weaknesses of industry technology,” said Gerdes. “Ford said go ahead and try to hack them and let us know how we can help with the research process.''
To achieve the goal of secure and efficient charging, Gerdes’ team proposes a design that implements both hardware and software solutions that will improve the charging station grid’s resiliency, coordinate remote updates, and respect end-user privacy.
The researchers will work with Hubject to examine the security of EV/EVSE communications. The German-headquartered company specializes in creating secure charging solutions for EV/EVSE so that customers feel confident about their data’s security. The collaboration will provide unprecedented access to EV communications for Virginia Tech and its partners, allowing them to examine some of the most sensitive portions of the vehicle charging process.
Gerdes’ research delves into several levels of cybersecurity risk. Local vulnerabilities could allow an attacker to gain control of a charger or a vehicle through charger-to-vehicle communications. As a result, the team’s research will seek to understand how infected electric vehicles and chargers could then be used to target the power grid on a larger scale.
The project, slated to run through the end of 2023, will include collaborations with academic researchers and industry partners with backgrounds in cybersecurity, transportation security, grid security and resilience, and more.
Students cracking the code
The Ted and Karyn Hume Center for National Security and Technology, based in Blacksburg and Northern Virginia, is the student-focused research and learning center within the Virginia Tech National Security Institute, and home of this cutting-edge EV security work. For traditional research projects or student design teams in which vehicles are involved, you might expect to see twisting wrenches and oil-soaked hands; however, the work completed in this garage bay looks quite different. Students are building circuits, writing code, interfacing with modems, and tackling much of the project from their laptops.
The undergraduate electrical and computer engineering students who have dedicated much of their time to this project are thankful for the hands-on experience they’ve gained.
Computer engineering senior Grant Hewett’s primary focus has been finding ways to hack into the Ford Mach-E and expose any vulnerabilities in the vehicle that potential attackers could use for nefarious purposes.
“I have been interested in cybersecurity since high school and have pursued that interest here at Virginia Tech,” said Hewett. “I saw an email go out about a project with cybersecurity in cars and applied for it because I thought it looked interesting. I knew about attacks that had already been done on cars and was excited to try it myself.”


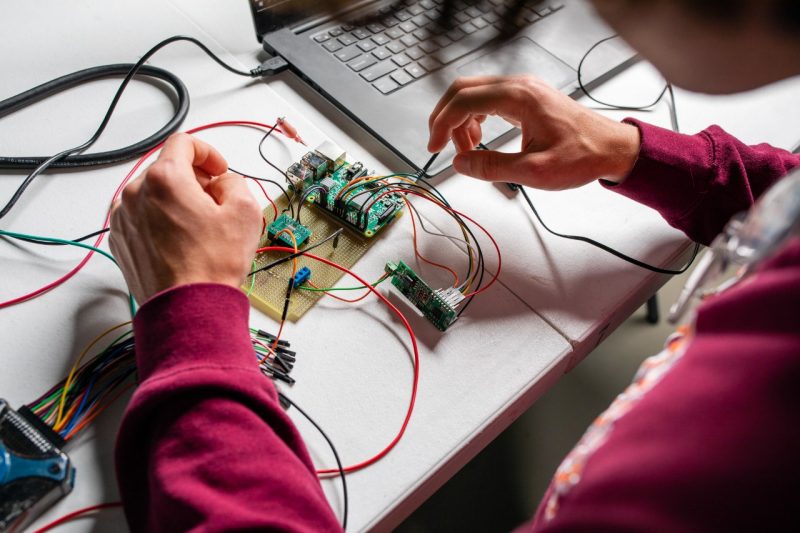
Hewett found that hacking a vehicle was more difficult than he originally expected because any previous vulnerabilities on the vehicle had been addressed and fixed by Ford. The team did find that the security in the charging procedure is not as robust as it could be. Charging stations have the ability to run the charging protocol with encryption, but some choose not to, leaving the traffic vulnerable to attacks.
Senior electrical engineering student Eric Wilson feels ready for life post-graduation thanks to his own problem-solving skills and self-guided work on the project.
“Unlike classwork, this stuff has never been done before. We can’t always rely on internet tutorials and documentation, which forces us to apply different problem-solving skills,” said Wilson. “At one point, one of our circuits had to interface with the charging port on the Mach-E, and simply connecting wires wasn't working. Since we didn't know what the issue was and we couldn't find the specific plug requirements, we took apart an existing charger plug and used the parts we needed.”
All the students involved also mentioned the support of Gerdes and how it made the project even more of a learning opportunity. “Dr. Gerdes is very knowledgeable in the field of automotive cybersecurity and guides our research efforts and keeps track of our progress,” said Wilson.
For Gerdes, this particular project couldn’t happen without the tireless work that these students put into the research almost daily.
“The students are willing to accept any challenge that I give them, and they always exceed my expectations when I ask them to do something. They are very ‘can-do,’ and it has been great to watch them overcome and mature and understand their role in the research,” said Gerdes. “This work that we are doing wouldn’t be possible without them.”
ECE students aren’t the only ones involved in the project. Max Fisher, a junior studying computer science, has enjoyed the project’s transdisciplinary approach. Fisher has spent his time hacking the internal communications on a Ford Focus Electric while Hewett and Wilson have been focused on the Mach-E, but sometimes their efforts overlap.
“Last semester, we were running tests of the attacks on the Focus, and Grant was a big part of that,” Fisher said. “We spent several hours together in the car running these attacks over and over. We would spend this time listening to WUVT on the car’s radio while driving around trying to run down its battery.”

Partnerships for success
Perhaps the most dynamic part of the research is the work that will be carried out on a real-world testbed that includes the Bronzeville Community Microgrid, a neighborhood in Chicago, Illinois. Using a Tritium charger capable of 350 kW and support from Commonwealth Edison Company, the testbed, which includes a vehicle emulator, will allow Gerdes and a collaborative team at Purdue University to create a scenario that mimics real-world potential threats to consumers at EV charging stations.
Other academic partners on the project include Utah State University and Georgia Tech.
A team from Utah State will create cyber-hardened converters for a more secure EV powertrain. Their work will then be augmented by Kyriakos Vamvoudakis, an assistant professor at the Daniel Guggenheim School of Aerospace Engineering at Georgia Tech and a former faculty member of the Kevin T. Crofton Department of Aerospace and Ocean Engineering at Virginia Tech. Vamvoudakis will implement control strategies based on machine learning and AI that will be coupled with intrusion detection and mitigation strategies to securely control the Utah State team’s converters.
Utah State will also provide access to two state-of-the-art facilities – a test track and a battery limits research lab – that support the project’s tasks.
The university’s electric vehicle and roadway research facility and test track allows for research into EV drivetrains, charging infrastructure, and micro-grid systems. The facility has a quarter-mile electrified test track, a 5,000-square-foot vehicle system integration facility equipped with 750 kVA service, solar power, grid-tied energy storage, and EV charging infrastructure.
Utah State’s Battery Limits and Survivability Testing Laboratory, known as the BLAST Lab, enables researchers to evaluate battery cell and pack performance and to safely validate and push battery limits to their physical limits. XFC technologies have the potential to overcharge batteries quickly, which could result in thermal runaway, making the lab’s capabilities critical to the research.
Berkay Celik and Antonio Bianch – both assistant professors in Purdue University’s Computer Science Department – will use their expertise on software systems security to design a custom “fuzzing” tool to uncover implementation flaws in the communication protocol used by EVs and chargers. The tool will inject unexpected or random data into the algorithms to detect bugs.
By simulating attacks on the Mach-E and also working to implement more secure systems that address vulnerabilities, Gerdes’ team is gaining an understanding of EV security from both ends of the spectrum. Creating a safe charging environment could result in an electrifying win for consumers and manufacturers.
“Currently, there are several questions regarding the security of EV-to-EVSE communication and the potential impacts XFC could have on the grid, and we want to help provide answers. This research will also raise the bar for attackers by proposing countermeasures that are difficult to defeat,” said Gerdes.
Photos and video by Peter Means
If you want to have an impact on our students and faculty like those featured in this magazine, go here to support the College of Engineering. For more information, call (540) 231-3628.
-
Article Item
-
Article Item
-
Article Item



